Coronavirus changed the way we work. Look no further than the continuing prevalence of hybrid and remote working. In fact, a March 2024 report published by Pew Research found that 14% of American adults—roughly 22 million people—work from home all of the time.
With remote work becoming commonplace, organizations need a way to reach each other and communicate when they’re not in the same physical space. The solution for many such organizations was and continues to be Microsoft Teams.
The Rise of Microsoft Teams
Microsoft rolled out Microsoft Teams in March 2017. Statista reports that there were a mere 2 million early adopters using the platform on a daily basis. Before the pandemic, this number had climbed to 20 million in 2019.
Then, the world changed.
Beginning in early 2020, lockdowns and remote work accelerated this growth. 75 million users in 2020; 145 million in 2021; 270 million in 2022. The most recent number at the time of this writing is 300 million daily users as of 2023.
#Millions Daily Microsoft Teams Users (2017-2023)
Data courtesy of Statista
Teams as a Vehicle for Phishing
Obviously, Microsoft Teams is not the first internet-based platform to become a forum through which cybercriminals conduct their business. Email and social media have also been used for criminal activity.
Like all software and applications, you need to ensure your security controls are updated to prevent potential security risks, Microsoft Teams is no different. Especially as Microsoft Teams has grown in popularity, it has provided yet another key resource you need to protect from threat actors as they seek to infiltrate your network.
Here are two stories of phishing through Microsoft Teams:
Midnight Blizzard
In May 2023, a Russian state-sponsored social engineering group known as Midnight Blizzard launched a phishing attack through Teams. Their goal was to steal user credentials. They did this by impersonating legitimate IT support organizations.
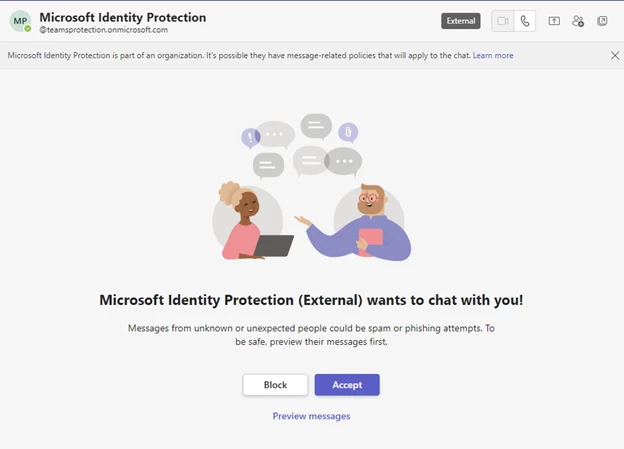
Screenshot of a Microsoft Teams message request sent from Midnight Blizzard to Teams users. Note the subdomain as it is one controlled by the malicious actor.
Microsoft Link to Midnight Blizzard Phishing Attack.
Phishing attacks are all about deception and looking like a legitimate contact. Midnight Blizzard did this through the subdomain “teamsprotection.onmicrosoft[.]com,” which is not a subdomain Microsoft actually uses.
Other possible malicious actor-controlled subdomains include:
| teamsprotection.onmicrosoft[.]com | identityverification.onmicrosoft[.]com |
| mlcrosoftaccounts.onmicrosoft[.]com | msftprotection.onmicrosoft[.]com |
| mlcrosoftaccounts.onmicrosoft[.]com | accountsverification.onmicrosoft[.]com |
| msonlineteam.onmicrosoft[.]com | azuresecuritycenter.onmicrosoft[.]com |
| msftservice.onmicrosoft[.]com | accounteam.onmicrosoft[.]com |
| noreplyteam.onmicrosoft[.]com |
Storm-0324
Storm-0324 is a financially motivated cybercrime group. They are in the business of ransomware-as-a-service (RaaS): gaining access to systems and then selling that access to other threat actors. After the hand-off, more dangerous follow-up attacks such as ransomware occur.
Beginning in July 2023, Storm-0324 was observed distributing “payloads” of phishing lure through Microsoft Teams. Specifically, they targeted organizations which allow their users to interact and share files externally, luring them with Microsoft SharePoint files. When users used and distributed the files, they inadvertently created an infection chain.

Microsoft Teams has proven itself a reliable tool for remote workers, but it must still be secured from threat actors.
Identifying and Defending Against Microsoft Teams Based Phishing Attacks
While standard anti-virus and indicators of compromise (IOC) software is typically enough to detect a malicious attack, at the time of this writing, Microsoft Teams lacks strong front-end intervention. In other words, Teams currently cannot strike down malicious content before the user has the chance to accept or deny the message.
So, it’s on you and your users to strike down these messages.
So, what can you do?
Shrink the Attack Surface
If you are licensed for Microsoft Defender for Office 365, you can increase protection. Just follow these steps. Need help? Contact Innovative Integration:
Log-in to the security center’s safe attachments configuration page at https://security.microsoft.com/safeattachmentv2.
- Press Global settings.
- Verify “Turn on Defender for Office 365 for SharePoint, OneDrive, and Microsoft Teams” is set to on.
- Navigate to the security center’s Safe links configuration page at.
- If you have multiple policies, you’ll need to complete this step for each policy.
- Select a policy, a flyout appears on the left-hand side.
- Press Edit protection settings.
- Check to make sure “Safe Links checks a list of known, malicious links when users click links in Microsoft Teams” is turned on.
- Press Save.
- In organizations with Microsoft Defender for Office 365 Plan 2 or Microsoft Defender XDR, admins can decide whether users can report malicious messages in Microsoft Teams.

Locking down your system’s settings will help prevent phishing attacks before they begin.
Defend
Microsoft offers several tips organizations can use to help reduce the risk of compromise. These include:
- Deploy phishing-resistant user authentication methods.
- Enforce specific access control combinations to restrict the authentication methods used before a user can gain access to a company’s digital resources.
- Enable Microsoft 365 auditing to gain visibility into potential phishing attempts.
- Restrict resource access to known business devices.
- Implement Microsoft’s conditional access app controls and cloud-delivered protections. Require multi-factor authentication (MFA) for file downloads and use AI to identify and prevent unknown or suspicious threats. Endpoint Detection and Response (EDR) solutions are also highly recommended.
- Audit and limit administrator-level service accounts. Using the least privileged access model and zero trust security are also recommended.
Evolve with the Threats
With every evolution and response cybersecurity teams make, bad actors adapt. What works today for your security may not work tomorrow, so it’s important for your organization to stay ahead of the curve.
If your business is one of the many using Microsoft Teams daily, you must be aware of the threats and be prepared to counter them at a moment’s notice.
That’s where a managed IT firm like Innovative Integration comes in. With our i3 suite of software solutions and our knowledge of Microsoft Security Controls, we give your team the backing it needs to fight off the threats that target it. Ready to learn more? Contact Innovative Integration — we look forward to helping you navigate the challenging waters of cyberspace.





