Cybersecurity has undergone significant transformations, forcing organizations to rethink their defense mechanisms. Historically, security models operated on a trust but verify basis, presuming that everything within the organization’s network could be considered safe. This traditional perimeter-based approach has been challenged by the dynamic nature of modern cyber threats, leading to the adoption of a more stringent model: Zero Trust. Now you have probably heard of Zero Trust security models. But you might be hesitant to overhaul your organization’s entire cybersecurity infrastructure for a concept that still seems new or unclear. Traditional security models, based on the principle of “trust but verify,” may have served well in the past when network boundaries were clear and well-defined. However, with the rise of cloud services, remote work, and increased mobility, these models are facing new challenges that they weren’t originally designed to handle.
5 Benefits of a Managed Service Provider – Watch Our Video
The Flaws of Traditional Security Models
Historically, cybersecurity relied heavily on perimeter-based security models that assumed everything inside the network could be trusted. This approach has substantial vulnerabilities:
- Internal Threats: Once inside the perimeter, malicious actors could move laterally with little resistance.
- Perimeter Erosion: With the adoption of cloud-based assets and services, defining and securing a perimeter has become increasingly difficult.
Such vulnerabilities expose organizations to significant risks, highlighting the need for a paradigm shift in how security is approached.
What is the Zero Trust Security Model?
Recognizing these insufficiencies, the cybersecurity industry is shifting towards the Zero Trust model, which operates under the principle of “never trust, always verify”. Zero Trust doesn’t just fortify the perimeter—it eliminates the concept of a perimeter altogether. Instead, it requires verification at every step, aligning security closely with modern business practices and technology use. You wouldn’t let someone into your house if you didn’t know who they were, right? Zero Trust security models is built upon the belief that threats can come from anywhere, trust must always be earned and never assumed. This approach marks a deliberate move from inherent trust to a model where consistent verification is foundational, treating every attempt to access the system or data as a potential threat until proven otherwise.
Zero Trust Security Models: Core Principles

Principle 1: Verify Explicitly
How?
- Implement Multi-Factor Authentication (MFA) to ensure that users are who they claim to be by requiring multiple forms of verification (something you know, something you have, something you are).
- Use device health checks to determine whether a device is secure enough to access resources. This includes checking for up-to-date security patches, whether the device is jailbroken/rooted, or if it has encryption enabled.
- Employ context-aware access controls that take into account the user’s location, device, network, and behavior patterns to make real-time decisions on access requests.
Why?
The benefit of explicitly verifying every access request is to dramatically reduce the risk of unauthorized access. By assessing multiple factors before granting access, you’re not only ensuring the identity of the requester but also the security posture of their device and the context of their request. This layered approach to security protects sensitive resources from breaches effectively, even if one factor (like a password) is compromised.
Principle 2: Least Privilege Access
How?
- Conduct regular access reviews to ensure users have only the permissions they need to perform their current roles. Remove unnecessary privileges that may have accumulated over time (privilege creep).
- Implement Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) to dynamically assign permissions based on the user’s role or attributes.
- Utilize just-in-time (JIT) access and privilege elevation for situations that require temporary access to sensitive resources, ensuring that users have elevated permissions only when necessary and for a limited time.
Why?
Granting users the minimum level of access needed to accomplish their tasks minimizes the attack surface and the potential damage from both external and internal threats. If a user’s account is compromised or an insider turns malicious, the impact is limited because they can’t access information or systems irrelevant to their duties. This principle is foundational to a strong security posture that focuses on damage control as much as prevention.
Principle 3: Assume Breach
How?
- Segregate network segments to contain breaches within isolated zones, preventing lateral movement across your IT environment.
- Implement strong detection capabilities, including anomaly detection, to identify unusual access patterns or behaviors that could indicate a breach.
- Establish a comprehensive incident response plan that includes clear roles and responsibilities, communication strategies, and recovery procedures to swiftly address and mitigate breaches.
Why?
The “Assume Breach” mentality shifts the focus from merely trying to prevent intrusions to also preparing for how to detect, respond to, and recover from them. It acknowledges the reality that organizations are constantly under threat, and some attacks may succeed. By planning for the inevitable, you ensure that when a breach occurs, its impact is minimized, operations can quickly return to normal, and data integrity is preserved as much as possible. This approach strengthens resilience against cyber threats, ensuring continuity and trust in your organization’s ability to protect its assets and stakeholders.
Zero Trust Architecture (ZTA)
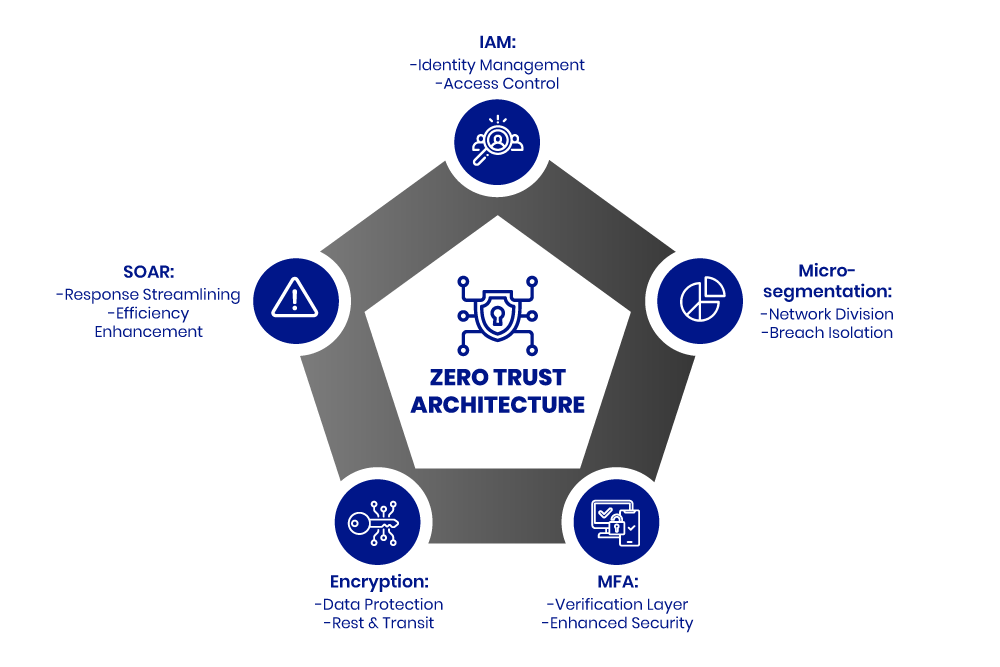
Zero Trust Architecture isn’t just a concept; it’s a comprehensive blueprint designed to fortify modern digital environments against cyber threats. Here’s a breakdown of its essential components, explaining what they are and their role in the architecture:
- Identity & Access Management (IAM): At the heart of Zero Trust security models is the ability to manage and verify who is trying to access your network. IAM is the framework that ensures only the right individuals can access the right resources at the right times for the right reasons. It’s about knowing and controlling identities, both human and non-human, within an organization.
- Micro-segmentation: Think of your network as a series of compartments rather than a single open space. Micro-segmentation divides the network into smaller, secure zones, making it easier to control access and limit the spread of any potential breaches. Each of these zones requires separate access permissions, ensuring that an attacker cannot move freely throughout your network after breaching a single point.
- Multi-factor Authentication (MFA): Beyond passwords, MFA requires one or more additional verification factors, adding a critical layer of security. This could mean a text message with a code, a fingerprint, or a face scan—anything that ensures that the person requesting access is who they claim to be.
- Encryption: Essential for protecting sensitive information, encryption secures your data both when it’s stored (at rest) and when it’s being transmitted (in transit). Even if data is intercepted or accessed without permission, encryption makes it unreadable and useless to those without the key.
- Security Orchestration, Automation, and Response (SOAR): This component handles how security alerts are managed and responded to. SOAR streamlines the processes involved in detecting, investigating, and mitigating potential security threats, making it easier for organizations to manage their security posture with efficiency and speed.
Zero Trust Model and The Cloud
The integration of Zero Trust security models becomes crucial with the shift towards cloud technologies. In the cloud’s shared responsibility model, both service providers and clients play active roles in security. Service providers manage the cloud infrastructure’s security, while clients are responsible for safeguarding their data within that infrastructure. This model highlights why adopting a Zero Trust approach is essential—since security responsibilities overlap, assuming trust in any component can create vulnerabilities. Zero Trust mitigates these risks by enforcing strict verification, no matter where the data resides or who is requesting access. This ensures a higher level of security that aligns with the complex, distributed nature of cloud services.
Zero Trust Security Models: A Strategic Necessity
The shift to Zero Trust security models is no mere trend. It is a fundamental change in how businesses approach cybersecurity. Its growing importance in an increasingly interconnected world cannot be overstated. Because of this importance, many businesses are turning to IT specialists to help support their cybersecurity infrastructure and posture. Innovative Integration understands the role of a secure IT environment for growing small and medium-sized businesses who are seeking continual growth.
From managed services to data security and recovery, and from data center modernization to application mobility, Innovative Integration has the IT support solutions! Ready to learn more? Contact us today to see for yourself the Innovative difference!